Mobile devices are everywhere these days. We use them to store and handle a lot of private information, like personal details, bank account info, health records, and more. Because they hold so much valuable data, mobile apps have become major targets for cyberattacks. If an app has security weak spots, it could lead to data leaks, money loss, and damage to a company's reputation.
For anyone involved in creating or testing software, making sure mobile apps are secure isn't just a good idea anymore – it's essential. This is where mobile security testing comes in. It's all about finding and fixing security risks in mobile apps before they cause problems.
What is Mobile Security Testing?
Mobile security testing is a specific type of software testing that checks how secure a mobile app is. The main goals are to find weak spots (vulnerabilities), make sure the app meets security rules, and protect both the app and its users from online threats.
It's different from other kinds of testing:
- Functional testing checks if the app's features work correctly.
- Performance testing checks how fast and stable the app is.
- Mobile security testing focuses on how well the app defends itself against attacks and protects user data.
Key Objectives:
- Find Weaknesses: Look for problems like storing data insecurely or having easy-to-guess logins.
- Stop Threats: Prevent bad things like data theft, unauthorized account access, or harmful software getting into the app.
- Meet Standards: Make sure the app follows rules like GDPR (for data privacy) or HIPAA (for health info) and industry guidelines like the OWASP Mobile Top 10.
- Build User Trust: Show users that the app is safe to use and respects their privacy.
Testing mobile apps is unique because phones and tablets have their own challenges. They have limited resources, connect to different hardware (like cameras and GPS), and run on various networks (like public Wi-Fi), all of which can create specific security risks.
Why Mobile Security Testing Matters
Protecting mobile apps is more important now than ever before:
- More Threats: Attacks targeting mobile devices are increasing. In 2023, mobile malware attacks reportedly went up by 50% compared to the previous year, often going after banking and social media apps.
- Sensitive Data: Apps often handle very private information like credit card numbers, passwords, and location data, which are exactly what hackers want.
- User Trust: If an app has a security breach, users lose trust quickly and might switch to a competitor. One survey found that almost 80% of users would delete an app after a security issue.
- Rules and Fines: Not following data protection rules (like GDPR) can lead to huge fines, pushing companies to take security seriously.
- Business Costs: Security breaches are expensive. On average, they cost companies millions of dollars globally, not even counting the customers they lose.
In Agile development, where apps are updated frequently, security testing needs to happen continuously. This ensures that new security holes aren't introduced with each update, balancing the need for speed with the need for safety.
Types of Mobile Security Testing
There are several ways to test mobile app security, each looking for different kinds of problems:
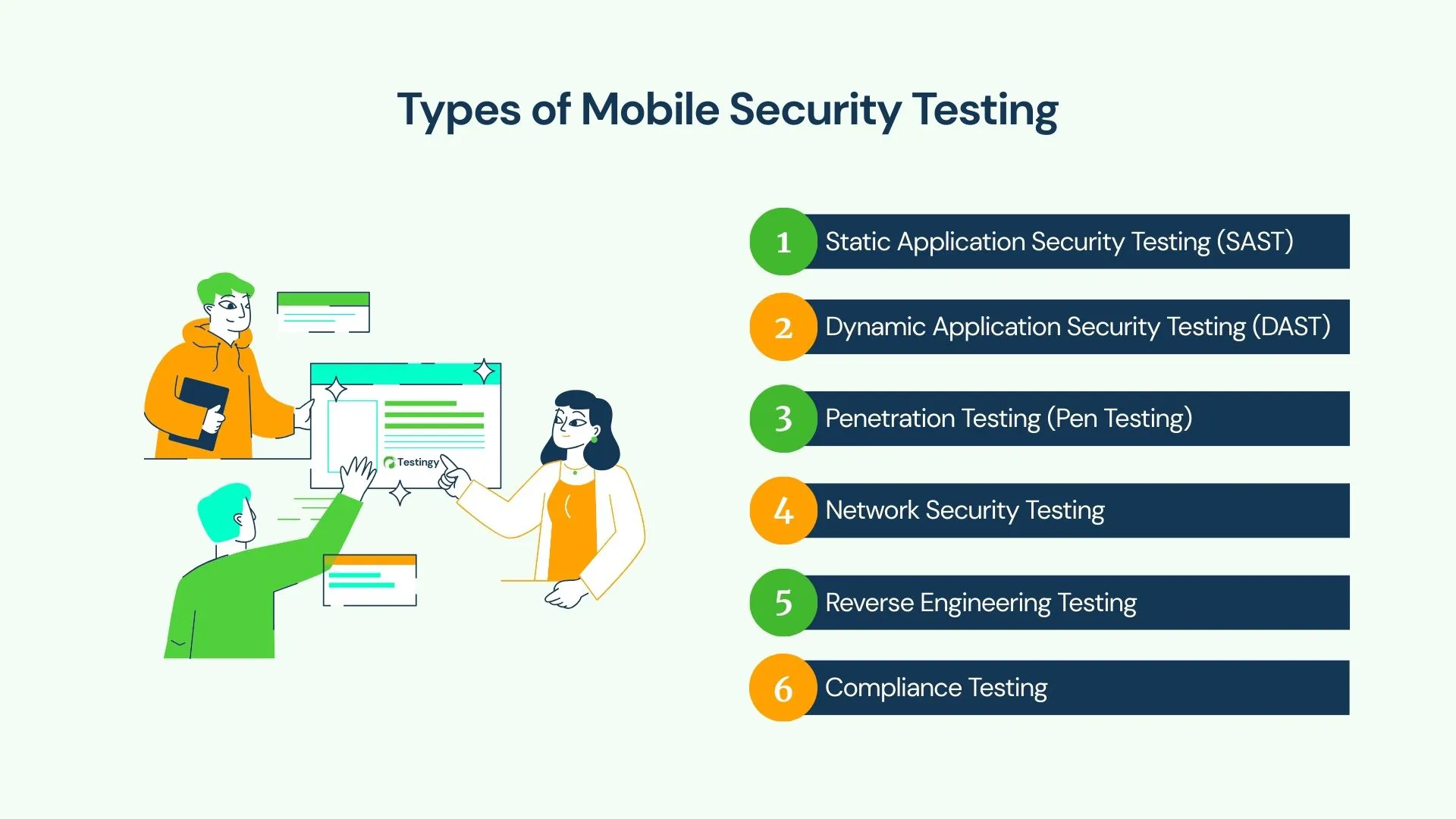
Static Application Security Testing (SAST)
- What it does: Looks at the app's source code or compiled files without running the app. Think of it like proofreading the code for security mistakes.
- Example: Searching the code for passwords or secret keys that were accidentally left in.
- Goal: Find security flaws early in the development process, when they are easier and cheaper to fix.
Dynamic Application Security Testing (DAST)
- What it does: Tests the app while it's actually running, either on a real device or an emulator. It acts like a user (or an attacker) interacting with the app.
- Example: Trying to trick a login form into revealing information it shouldn't by entering malicious commands (like SQL injection).
- Goal: Find security problems that only show up when the app is running.
Penetration Testing (Pen Testing)
- What it does: Simulates a real hacker trying to break into the app. Ethical hackers use their skills to find and exploit weaknesses.
- Example: Trying to break the app's encryption to read data being sent between the app and the server.
- Goal: Discover security holes that could actually be used by attackers.
→ Related article: Penetration Testing Explained: A Developer and QA Tester’s Security Guide
Network Security Testing
- What it does: Checks how securely the app sends and receives data over networks (like Wi-Fi or mobile data).
- Example: Checking if the app sends sensitive information without encryption when connected to a public Wi-Fi network.
- Goal: Prevent attackers from spying on or interfering with the app's communication (known as Man-in-the-Middle attacks).
Reverse Engineering Testing
- What it does: Tries to take the app apart (decompile it) to understand how it works and find hidden secrets.
- Example: Taking an installed app file (like an Android APK or iOS IPA) and trying to extract sensitive information like API keys from the code.
- Goal: Make sure the app's code is properly protected (obfuscated) so it's hard for attackers to understand and tamper with.
Compliance Testing
- What it does: Checks if the app follows specific security rules and standards (like OWASP, PCI DSS for payments, or HIPAA for health).
- Example: Making sure the app automatically logs users out after a period of inactivity to prevent unauthorized access.
- Goal: Ensure the app meets all necessary legal and industry security requirements.
Common Mobile Security Threats
The OWASP Mobile Top 10 list highlights common dangers that mobile security testing aims to find and fix:

- Improper Credential Usage: Handling logins (passwords, keys) insecurely, allowing theft and impersonation.
- Inadequate Supply Chain Security: Vulnerabilities entering via third-party code/libraries, compromising the app.
- Insecure Authentication/Authorization: Weak login processes or permission checks, allowing unauthorized access.
- Insufficient Input/Output Validation: Not checking data properly, leading to injection attacks (e.g., SQLi, XSS) that steal data or control the app.
- Insecure Communication: Sending sensitive data without strong encryption (HTTPS/TLS), risking interception on networks like public Wi-Fi.
- Inadequate Privacy Controls: Mishandling user data, violating privacy regulations and user trust.
- Insufficient Binary Protection: Lack of protection against code analysis (reverse engineering) or modification, risking intellectual property theft or malicious app versions.
- Security Misconfiguration: Errors in security settings (app or server), creating accidental vulnerabilities.
- Insecure Data Storage: Storing sensitive data on the device without proper encryption, making it accessible if the device is compromised.
- Insufficient Cryptography: Using weak or flawed encryption methods, failing to properly protect data even if encrypted.
Testing helps find and fix these issues early, making the app much harder to attack.
Tools for Mobile Security Testing
Many tools can help with mobile security testing:
Appium (with Security Extensions)
- While primarily for automating functional tests, Appium can be used to automate security checks, like testing how the app handles bad input or trying many login attempts.
- Use Case: Writing a script to automatically try common weak passwords or SQL injection attacks on the login screen.
Burp Suite
- A powerful tool that sits between the app and the internet, allowing testers to see, modify, and replay the network traffic the app sends and receives. Great for DAST and penetration testing.
- Use Case: Testing an online shopping app to see if payment details are sent securely or if communication can be intercepted on insecure Wi-Fi.
OWASP ZAP (Zed Attack Proxy)
- A free, open-source tool similar to Burp Suite, often used for automatically scanning web applications (including mobile apps that use web components) for common vulnerabilities.
- Use Case: Automatically scanning the parts of a mobile app that load web content to find common web flaws like XSS.
MobSF (Mobile Security Framework)
- An all-in-one open-source tool that can perform static analysis (SAST) by examining app files (APK for Android, IPA for iOS) and some dynamic analysis and reverse engineering tasks.
- Use Case: Analyzing a banking app's code (without running it) to find hardcoded passwords or insecurely stored data.
Frida
- A dynamic instrumentation toolkit. It allows testers to inject scripts into running apps to see how they behave internally, modify their logic on the fly, and bypass security controls for testing purposes.
- Use Case: Temporarily disabling security features like SSL pinning (which normally prevents traffic interception) to allow tools like Burp Suite to analyze the app's encrypted traffic.
Drozer
- A security testing framework specifically for Android apps. It helps assess risks related to how the app interacts with the Android operating system, like checking for exposed app components or data leaks between apps.
- Use Case: Checking if sensitive parts of an Android app can be accessed by other malicious apps installed on the same device.
Cloud-Based Testing Platforms (e.g., BrowserStack App Live, Sauce Labs)
- Provide access to a wide range of real mobile devices (iOS and Android) hosted in the cloud. Testers can run their apps and security tools on these real devices remotely.
- Use Case: Running penetration tests or dynamic scans on many different device models and OS versions without needing to own all the physical devices.
Using a combination of these tools often provides the most comprehensive security testing coverage.
Mobile Security Testing in Agile Development
Agile development focuses on rapid, iterative releases. To keep up, security testing must be woven directly into this fast-paced cycle, rather than being an afterthought. Here’s how:
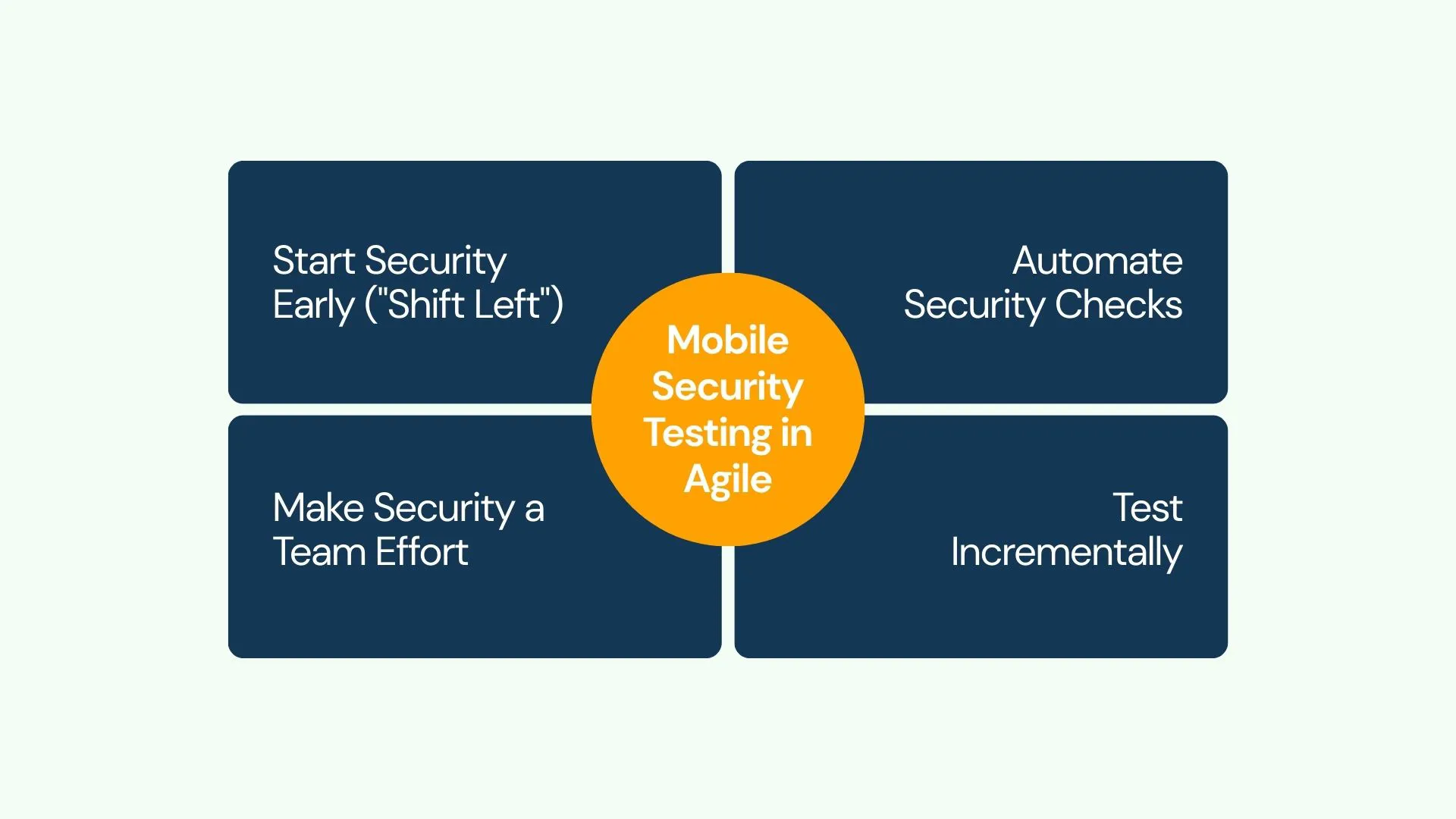
Start Security Early ("Shift Left")
Don't wait until the end of development. Integrate security thinking and basic checks right from the beginning.
Automate Security Checks
Manual testing can't always keep pace with Agile sprints. Automate routine security tests (like scanning code for known flaws or checking for insecure configurations) and include them in your regular build process (CI/CD pipeline).
Make Security a Team Effort
Security isn't just one person's job. Developers, testers, and security specialists need to collaborate. Developers should focus on writing secure code, while testers actively look for ways to break security.
Test Incrementally
Tackle security testing in manageable chunks within each development cycle (sprint). Focus on the security aspects of the features being built or modified in that specific sprint, gradually building up the application's overall security posture.
A team might use MobSF to scan an APK in Sprint 1, fix vulnerabilities in Sprint 2, and pen-test with Burp Suite in Sprint 3—all within Agile timelines.
How to Conduct Mobile Security Testing (A Practical Process)
Here’s a step-by-step approach to performing mobile security testing:
1. Define the Scope: Figure out what needs testing the most.
- Identify the most critical parts of the app, like login pages, payment processing, or areas handling personal user data.
- Set clear goals, such as "Prevent unauthorized users from accessing account information" or "Ensure all payment data is encrypted during transmission".
2. Prepare the Test Environment: Get everything ready for testing.
- Decide whether to use real physical devices, emulators/simulators (software that mimics devices), or cloud-based device platforms. A mix is often best.
- Install the necessary testing tools (like MobSF, Burp Suite, Appium, Frida) on your test machine or within your testing environment.
3. Perform Static Analysis (SAST): Check the code without running the app.
- Use a tool like MobSF to analyze the app's package file (APK for Android, IPA for iOS).
- Look for common issues like hardcoded passwords or API keys, insecure code practices, or known vulnerabilities in included libraries.
4. Execute Dynamic Testing (DAST): Test the app while it's running.
- Interact with the app as a user (or attacker) would. Use tools like Burp Suite or OWASP ZAP to intercept and analyze network traffic between the app and its server. Look for unencrypted data, weak authentication, or flaws in how the app handles sessions.
- Test input fields (like login forms or search bars) for vulnerabilities like SQL injection or XSS by entering specially crafted malicious input. You can automate some of this using scripts with tools like Appium.
python
from appium import webdriver
desired_caps = {
"platformName": "Android",
"deviceName": "emulator-5554",
"app": "/path/to/app.apk"
}
driver = webdriver.Remote("http://localhost:4723", desired_caps)
driver.find_element_by_id("login").send_keys("'; DROP TABLE users; --")
driver.find_element_by_id("submit").click()
result = driver.find_element_by_id("error").text
assert "Invalid" in result # Check for SQL injection protection
driver.quit()5. Conduct Penetration Testing: Act like a real attacker.
- Combine information from static and dynamic testing to try and actively exploit identified weaknesses.
- Use tools like Burp Suite to manipulate network requests or Frida to interfere with the app's runtime behavior, attempting to bypass security controls or access sensitive data.
6. Analyze Findings and Report: Document everything.
- Carefully record all vulnerabilities found, including how to reproduce them and the potential impact (e.g., "Low Severity: Debug messages visible" vs. "Critical: Unencrypted password transmission").
- Prioritize the findings based on risk, so the development team knows what to fix first. Provide clear recommendations for fixing each issue.
Benefits of Mobile Security Testing
Investing time in mobile security testing brings significant advantages:
- Reduced Risk: It's the most direct way to find and fix security holes before attackers can exploit them, preventing costly data breaches and data loss.
- Increased User Confidence: When users know an app takes their security seriously, they are more likely to trust it with their data and continue using it. A reputation for security can be a competitive advantage.
- Regulatory Compliance: Helps ensure the app meets legal and industry requirements (like GDPR, HIPAA, PCI DSS), avoiding potentially large fines and legal trouble.
- Cost Savings: Finding and fixing security flaws early in development is far cheaper and easier than dealing with the aftermath of a security breach after the app is released (which involves incident response, recovery costs, reputational damage control, etc.).
- Protecting Brand Reputation: A secure app protects the company's image. For example, a health app that securely handles patient data maintains its credibility and trustworthiness.
Challenges in Mobile Security Testing
While important, mobile security testing isn't always easy:
- Device Fragmentation: There are thousands of different mobile devices, operating system versions, and screen sizes. Testing on all of them is impossible.
- Evolving Threats: New attack methods and vulnerabilities appear all the time. What was secure yesterday might not be today.
- Resource Constraints: In fast-paced Agile environments, there might not be enough time or budget allocated for thorough security testing.
- Tool Limitations: No single security tool can find every possible vulnerability. Each tool has its strengths and weaknesses.
- Skill Gap: Effective security testing requires specialized knowledge and skills that not all testers or developers possess.
Best Practices for Mobile Security Testing
To make mobile security testing effective, follow these key practices:
- Start Early (Shift Left): Don't wait until the end. Integrate security considerations and testing activities right from the beginning of the development lifecycle (Sprint 1 in Agile).
- Automate Where Possible: Use automated tools (like Appium for UI checks, ZAP/Burp for scanning) for routine and repetitive security checks. This frees up testers for more complex manual testing. Integrate these tools into your CI/CD pipeline.
- Follow Industry Standards: Use established guidelines like the OWASP Mobile Top 10 as a checklist to ensure you're covering the most common and critical risks.
- Test Realistically: Don't just run automated scans. Simulate real-world attack scenarios, such as trying to intercept data on an insecure network (Man-in-the-Middle attack) or attempting to bypass login procedures.
- Promote Secure Coding: Security isn't just about testing; it starts with development. Encourage and train developers to write secure code from the start, such as always encrypting sensitive data and validating all inputs properly.
- Monitor After Launch: Security doesn't stop once the app is released. Consider using tools or services that monitor the app in production for suspicious activity or new threats.
Example: For a payment app, use Testingy’s Test Management to organize test cases for Appium login tests, MobSF code scans, and Burp Suite penetration tests, ensuring encrypted data.
Case Study: Security Testing in Action
Let's look at a simplified example: A team is building a new ride-sharing app.
- Goal: Ensure the driver login process is secure and that payment information transmitted through the app is protected.
- Tools Used: Appium for automating login tests, MobSF for static code analysis (SAST), and Burp Suite for manual penetration testing of network traffic.
- Testing Process:
- Automation: Appium scripts were run to test the login screen against common injection attacks and brute-force password attempts.
- Static Analysis: MobSF scanned the app's code and found an API key accidentally left exposed in a configuration file.
- Penetration Testing: Using Burp Suite, a tester intercepted the network traffic during a simulated payment and discovered the payment details were being sent without strong encryption.
- Result: The development team fixed the issues. They removed the hardcoded API key and implemented strong encryption for all payment-related API calls.
- Retesting: The security tests (Appium, MobSF scan, Burp Suite check) were run again to confirm the fixes were effective.
- Outcome: The secure login and payment features were successfully completed and included in the app release within the team's two-week Agile sprint cycle.
Conclusion
Mobile security testing isn't optional; it's a fundamental part of building trustworthy and successful mobile applications. In Agile development, integrating security testing with tools like Appium, Burp Suite, and MobSF, managed through Testingy’s platform, keeps apps secure without slowing progress.
As we rely more and more on mobile apps, mastering mobile security testing helps ensure the apps we build are not just functional and user-friendly, but also strong enough to protect users and businesses from ever-present online threats.